Encryption sounds powerful and somehow mystical. Encryption is the almighty solution when it comes to protecting your digital data. At the same time, many use it without fully understanding it. But who cares as long as it works.
Is encryption always the solution? How can I encrypt different kinds of data? And what if I no longer know my password?
To start, we will clarify a few things. First, not all encryption methods are the same. There are a million ways to perform encryption. Depending on the need, we look for different encryption algorithms, which are either fast, or slow, or strong, or weak, or even undecryptable. We won’t go into all possible encryption algorithm, but note that the strength of your encryption depends on the algorithm you use.
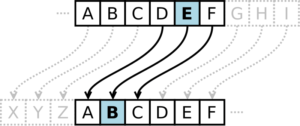
This is also encryption, but not secure at all: Ceasar cipher shifts the alphabet and reassigns each letter to a new one.
Secondly, there is an important aspect that is often forgotten. Encryption should be the last thing to protect your data and only kick in after everything else has failed. It’s great if all your devices are fully encrypted, but this encryption protects your data only from the moment your device has left your possession. We should, therefore, do our best to protect the devices that hold our data physically.
We can also encrypt data that we send to other people. Be it a picture sent on Whatsapp, a PDF sent by email or a file uploaded to Dropbox. We usually don’t want to share our messages and pictures with everyone. By encrypting the data we send out, we make sure that only the desired persons can access it.
And lastly, a quick glimpse into the data that we send out without noticing. Whenever you visit a website, there are so many metadata that are generated: your location, the page you visit, the time, your device settings, your keyboard settings, cookies, fingerprints, etc. Same if you upload a picture to your cloud. This picture contains information about the data and location when it was taken, but also about your camera, the aperture time, or the battery status. We can protect most of the data we create by encrypting it. When we share data, we want to transfer it through an encrypted channel, e.g. a VPN, end-to-end encryption or at least HTTPS.
Enough of the motivation, I think you get why encryption is essential. So, let’s come to solutions. For the threats briefly mentioned above, we have collected a short summary of software, which helps you protect your data.
1. Use end-to-end encrypted messengers like Wire. Messages are encrypted between sender and receiver, and nobody can read them in between. Since you are connected with your conversation partner over service, key exchange happens automatically, and you don’t have to worry. Other solutions besides Wire are Signal, Telegram or Threema.
2. Encrypt emails with PGP or let Protonmail do it for you. Your emails including all sensitive attachments can be intercepted and read without you noticing. Especially confidential material should never leave unencrypted. It is a bit more advanced if you do it on your own because you have to get the public key of the receiver. And it requires that both parties have encryption keys. When sending messages between Protonmail addresses, they take care of the encryption, and you can relax.
3. For securing data on your computer, you can encrypt it. Locally encrypted containers or entire encrypted drives can be created with VeraCrypt. VeraCrypt creates drives, which are fully encrypted and encrypts all files copied into that drive. When creating a new encrypted container, it guides you through all the steps and allows you to choose the encryption algorithm.
4. “There is no such thing as a cloud, it is just someone else’s computer.” Therefore, if you still need to upload files to cloud storage, you might consider encrypting all your data before uploading them. Boxcryptor automatically encrypts everything before sending it to the cloud.
5. A VPN encrypts all your moving data that quits or enters your device. This will therefore also encrypt the traffic that contains your unencrypted emails and the sites you visit. A hacker in a local network or your internet service provider can therefore not see the sites you visit or the messages you share.

If you loose your encryption key, you are locked out and loose your data.
Finally, whatever is encrypted can only be decrypted by knowing the correct key. Many services perform encryption and automatically manage the encryption keys, like in end-to-end encrypted messaging. If you manage the keys on your own like with PGP or VeraCrypt, keep them safe and don’t lose them. Once you forget your password, your data will also be inaccessible to you.




